With thriving of Internet, we are fulfilled with enormous amount of
data. And security is one of the important aspect we need to tackle for
the data we send over internet. Sharing of digital contents like image
over internet in a secure fashion is a challenge with numerous attacks
present. So, storing data on a single space and transmitting over it
isn’t much more secure than it used to be. On distributed system, we
have as much space but when it come with time we are always limited.
Problem Statement
Storing image in multiple locations make it available to be access from different locations. But because of the numerous attacks present, storing images on medium as a single file is not the security we need. On storing in multiple medium directly, the images might be easily accessible for user in faster way. But having a security issue in any one of the medium might lead to exposure of the image that might be crucial to users. Storing in a symmetric key encryption might be a solution that stores data encrypted and returns with some decryption algorithm with the given key. If the key is found, this may lead to finding the data along with other data within the medium. So, this simple solution doesn’t sound to be optimal.
Different secret image sharing algorithm has been proposed that help solving the problem by dividing images into shadow images that has absolutely no relation to original image. But operating on each pixels is a tedious job. So, some algorithm mitigated by decreasing the operation by applying DWT on image and reducing the operation by some amount. Still the fact remain that each pixels needed to be individual operated for those images.
Objectives
- To examine secret image sharing scheme by applying SVD for faster operation on generation of secret image shares as shadow words.
- To develop efficient way of generating shadow words from the generated share of SVD
- To analyze performance with other algorithms against time and error.
Overview
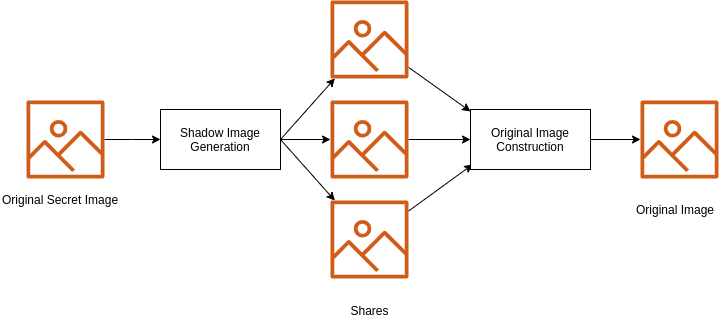
Every image or any sharing algorithm consists for original images, r shares of images where n number of shares are required to collect back the original image.
Methodology
Forward Process
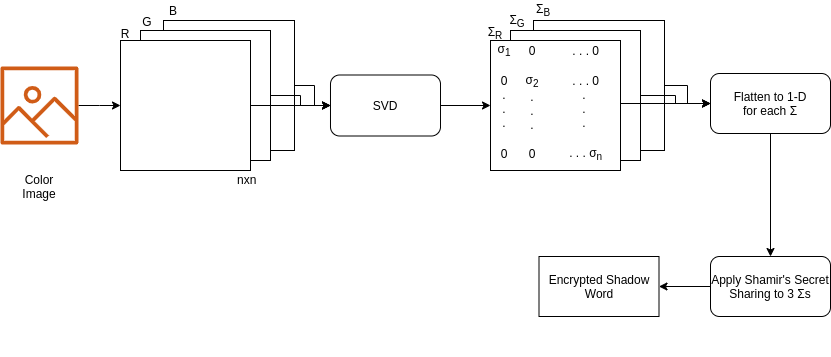
The forward operation generates shadow words that can be shared among multiple places.
Reconstruction Process
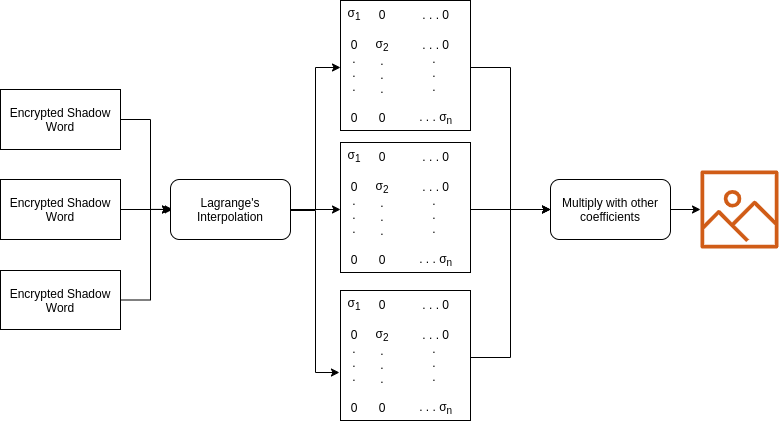
We collect n shares of shadow words and generate original image multiplying with other coefficients.
Conclusion
This research applies a simple theory applying lesser the operation, less the time taken by system to process the image. Given with decrease in operations, decrease in time; operating on n 2 operations, operating diagonally makes the operation decrease to n operations. Performance of purposed model is examined by performing series of experiments on available image data set in comparison with the referenced model.
The average time taken by proposed algorithm was found to be 0.5519s whereas in existing method without any transformation took 9.2005s and with increase in transformation level the time taken decreased to 6.1006s, 3.6295s and 1.8777 for L1, L2 and L3 transformations respectively.
MSE for the proposed method is found to be 0.79 in average where as without any transformation MSE is found to be 0.38. With increase in transformation, error seem to be increasing with decrease in time but the error is high because of ignoring of other band values during the transformation as 19.69, 31.48, 43.35 per pixels respectively.
The experiment is carried out primarily to decrease the time by decreasing the number of operations. Though the loss is slightly larger in comparison to spatial but the difference in time makes a huge difference. The loss increases as the transformation level increases which doesn’t happen to be the case in this experiment.
Limitation and Future Enhancements
Unlike other algorithms that has output as shadow image i.e. file being a regular image file that cannot be read, output in this algorithm is shadow word i.e. some large numbers store in file. With shadow words in action, other parameters need to be stored separately making the mediator file size huge.
Future work will be to implement the shadow image in current context. Solving some equations to generate shadow image will solve the file size issue too making it time efficient and lesser loss.